

Sikelelo provides over 600 Cybersecurity and ICT on-line training courses, laboratories and simulations. In addition we offer 2000 + Cybersecurity awareness solutions and professional services.

On-line Training
600 + on-line learning Cybersecurity and ICT courses including learning paths with real-life simulations. For ICT professionals, engineers, students and educators. Training for CompTIA, (ISC)², ISACA, EC-Council, Cisco, AWS, ITIL, PMP and other globally recognized certifications.
Professional Services
Sikelelo provides enterprise
business transformation and
corporate ICT professional services
on a turn-key or reimbursable basis
differentiated by price point,
experience and capability.

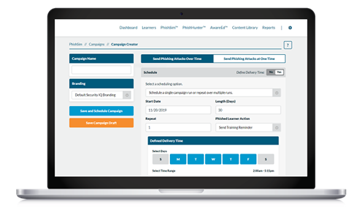
Cybersecurity Awareness
Continuous cybersecurity awareness
training, 2 000 + online resources
segmented by industry for
continuous security awareness.
Supplemented with phishing
simulation, assessment, quarantine
and management tools.
Access our On-line Training anytime anywhere
Learning Paths (42) ☰
Ethical Hacking
Network Traffic Analysis
Incident Response
OWASP Top Ten
Secure Coding Fundamentals
Linux Fundamentals
Network Security Fundamentals
Web Application Pentesting
Cybersecurity Management
ITIL Foundation
Project Management
and more...
Nice Workforce Categories (320) ☰
Securely provision (64)
Protect and defend (62)
Operate and maintain (46)
Analyze (44)
Oversee and govern (43)
Investigate (35)
Collect and operate (26)
Certifications (31) ☰
(ISC)² (6)
AWS (1)
CERT (1)
Cisco (2)
CompTIA (7)
EC-Council (1)
IACRB (6)
ISACA (3)
ITIL (1)
Juniper (1)
Microsoft (1)
PMI (1)
Cybersecurity Roles (84) ☰
Cybersecurity specialist (23)
Cybersecurity manager (15)
Penetration tester (9)
Cybersecurity analyst (7)
Cybersecurity architect (7)
Cybersecurity engineer (7)
Cybercrime investigator (6)
Incident analyst / responder (4)
Cybersecurity consultant (3)
IT auditor (3)
End to end busines transformation and technology transformation services
- Business case development
- Financial benefits realization
- Merger and Acquisition (M&A)
- Target Operating Model (TOM) Implementation
- Capability Maturity delivery
- Skills augmentation
- Delivery assurance
- Program Remediation
- Forex exposure transformation
- Reference rate advisory and implementation
- Information Technology Service Management
- Enterprise Service Management
- Data Management
- Turn-key or reimbursable application development
- Service Integration and Management advisory and implementation
- Supplier consolidation
- Sourcing management

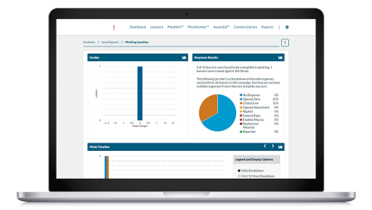
Cybersecurity Awareness to stay safe at work and home
Content types (642) ☰
Training Modules (331)
Posters (116)
Assessments (94)
Infographics (36)
Animated Modules (20)
Emails (20)
Live-Action Videos (19)
Program Plans & Kits (6)
Categories (533) ☰
Malware & Phishing (108)
Compliance (81)
Physical Security & Hardware (62)
Privacy & Data Protection (62)
Social Engineering (47)
Web-Based Threats (46)
Network Security (38)
Mobile Security (33)
Password Security (30)
Application Development (26)
Industries (599) ☰
All (483)
Healthcare (47)
Government and military (19)
Financial services (18)
Education (15)
Retail (9)
Manufacturing, construction (6)
Technology (2)
Packs (684) ☰
Plus (267)
Core (157)
Free (78)
Compliance (53)
Healthcare (41)
Privacy (22)
Developers (17)
Financial Services (17)
IT & Security (17)
Education (15)
Roles (634) ☰
General (529)
Developers (29)
Managers (25)
Executives (23)
Human resources (21)
IT staff (7)